Learn about the security risks associate with using public Wi-Fi and review practical tips to ensure your digital safety while on the road.

|
October 12, 2023 INSIDE THIS ARTICLE, YOU'LL FIND: |
In a world where staying connected is paramount, public Wi-Fi spots have become ubiquitous. These convenient networks offer an instant gateway to the online world, where you can connect with family and colleagues alike. But with convenience comes a crucial concern: Is public Wi-Fi safe?
Safety is a paramount and oft-cited concern of the travel experience, as airports, hotels, and other infrastructure promise to keep you safe. That said, public Wi-Fi is one area where a combination of vulnerabilities and user error can still result in an invasion of your privacy and exploitation of your data and finances.
Today, when you connect to internet hotspots at an airport terminal to check your email, or browse your credit card statements using your hotel’s network, there’s a possibility that you’re putting yourself and your organization at risk – especially if your browsing takes you to unencrypted websites. These days, website encryption scrambles your data and makes it unavailable to hackers, but taking extra precautions ensures your data won’t be compromised. (For example: Check your address bar for a lock symbol to see if a site is encrypted.)
While the average cost per lost and stolen documents is $225 for an individual, in a wide-scale corporate breach (50,000+ compromised documents) the average cost is $6.3 million. Even worse, according to the Ponemon Institute, once a breach has occurred, there is a 27.7% probability of a recurring material data breach over the next two years. So, what are the risks associated with public Wi-Fi and how can you mitigate them?
Can People See What I Am Doing on a Public Wi-Fi Network?
The short answer to this question is yes: It is possible for others to access your personal information or monitor your activity when using public Wi-Fi.
Public Wi-Fi networks are generally less secure than private networks, making them attractive targets for hackers and cybercriminals.
In addition, administrators of a public Wi-Fi network, not to mention criminals, potentially have the ability to see what users are doing while connected to their network, depending on the network setup and monitoring tools they have in place. Here's how it works:
- Network Traffic Monitoring: Network administrators can use specialized software to monitor the traffic flowing through their network. This includes the websites users are visiting, the data being transferred, and sometimes even specific content being accessed.
- Packet Sniffing: With certain tools, administrators and bad actors can capture and analyze packets of data that are being transmitted between devices on their network. This can potentially reveal the URLs of visited websites, search queries, and other data.
- Deep Packet Inspection (DPI): Some advanced network monitoring tools allow administrators to perform deep packet inspection. This means they can analyze the contents of data packets, potentially revealing the actual content of web pages, emails, and other online activities.
Even if you are reasonably sure that the network you're using is safe from oversight, there are other potential concerns that arise when using a public network.
What Security Risks Does a Public Wi-Fi Connection Pose?
How exactly do cybercriminals exploit the open nature of public Wi-Fi networks? There are a variety of risks to your personal information, all of which should be top-of-mind while using a public hotspot.
1. Man in the Middle Attacks
A Man in the Middle attack (MitM attack) is an event whereby a cybercriminal intercepts data as it travels between two parties. The attacker can then:
- Eavesdrop on all internet use, communications, and data transfers
- Redirect the victim’s communications to fake websites resembling banks, corporate sites etc. to obtain log-in credentials
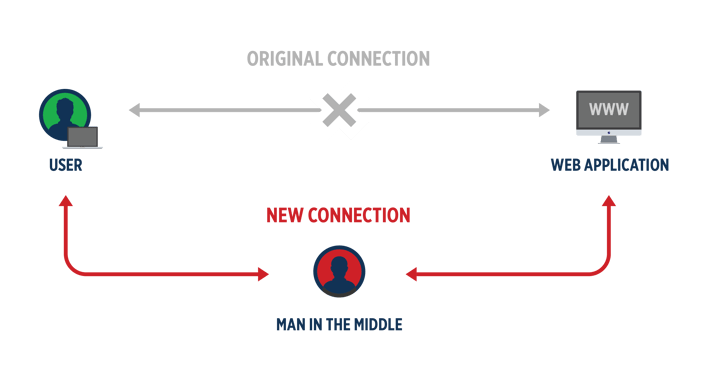
Source: Imperva
2. Snooping and Sniffing
Similar to MitM, snooping and sniffing is when hackers employ software kits enabling them to eavesdrop on Wi-Fi signals. This allows cybercriminals to monitor everything you do online, allowing them to capture log-in credentials and even hijack your accounts.
3. Malware Distribution
Hackers can infect your device with malicious software in several ways:
- Using unsecured Wi-Fi connection to distribute malware
- By creating an ad hoc peer-to-peer network between you and the hacker, if your device is set to “discover new networks,” it is possible for cybercriminals to forge a direct link to your device
- Once on your network, a hacker can send you fake install update notification, where you download malware directly onto your device
- Using worms. Unlike viruses, worms need not be downloaded onto your device, rather they can be spread from computer to computer within a public Wi-Fi network
4. Fake Hotspots
Using an innocuous or reputable name, rogue access points fool victims into signing onto hackers’ rogue networks. Hackers then can record all keystrokes to gain valuable information, including passwords.
5. Credential theft
Public Wi-Fi networks can be used by attackers to launch phishing attacks aimed at stealing login credentials for various accounts. Users who unknowingly provide their usernames and passwords on such networks can have their accounts compromised.
What Can Travelers Do to Protect Themselves When Using Public Wi-Fi?
Follow these recommendations to limit others' ability to compromise your device:
- Only Visit Sites Using HTTPS: Prioritize websites that use HTTPS encryption when browsing on public Wi-Fi. The padlock icon in your browser's address bar indicates that your connection is secure, safeguarding your data from interception and tampering. Again, visiting encrypted websites on a public network is generally safe, though following best practices still applies.
- Use a Virtual Private Network (VPN) to Secure Your Public Wi-Fi Connections: Yes, using a VPN protects you on public Wi-Fi. The VPN service encrypts your internet traffic, ensuring that your sensitive data remains shielded from prying eyes and potential hackers.
- Disable File Sharing: Turn off file sharing settings on your device to prevent unauthorized access to your files and folders by other users who might be connected to the same public Wi-Fi network.
- Log Out of Accounts When Done Using Them: Always log out of your accounts after you've finished using them, especially when connected to public Wi-Fi. This prevents unauthorized access to your accounts in case your device falls into the wrong hands.
- Limit Your Sensitive Activity While Using Public Wi-Fi: Exercise caution when accessing sensitive information such as online banking or entering credit card details while connected to public Wi-Fi. Minimize these activities or use a secure personal hotspot to mitigate the risk of data interception.
- Protect Your Device with Up-to-Date Antivirus Software: Ensure your device is equipped with the latest antivirus software. Regularly update your antivirus definitions to defend against malware and other security threats that could potentially target your device over public Wi-Fi.
- Avoid Networks That Aren't Password Protected: Avoid connecting to Wi-Fi networks that are open and lack password protection. These unsecured networks are susceptible to various security breaches, making your data vulnerable to interception and hacking attempts.
- Don't Allow Your Wi-Fi to Auto-Connect to Networks: Disable the auto-connect feature on your device to prevent it from automatically connecting to any available Wi-Fi network. This safeguards you from unknowingly connecting to rogue or malicious networks that cybercriminals may set up.
- Don't Use an App to Access Sensitive Information: Instead of using apps to access sensitive information like banking or financial services over public Wi-Fi, opt for the browser version of the service. This reduces the risk of exposing your data to potential app vulnerabilities.
- Leave Your Wi-Fi or Bluetooth Off If You Are Not Using Them: Turning off Wi-Fi and Bluetooth when not in use prevents your device from automatically searching for and connecting to networks, reducing the chances of unintentional exposure to security risks.
The allure and ease of public Wi-Fi can't be denied. However, it's crucial to acknowledge the potential security risks that come with it. By arming yourself with knowledge and following the practical tips outlined in this guide, you can confidently navigate the digital realm while on the go, protecting your personal data and online privacy.
Remember, being proactive about your cybersecurity is paramount, especially when traveling. If you're seeking expert guidance and personalized solutions to bolster your travel security, reach out to Global Guardian. Find out how our team can support your security needs: For assistance, call our 24/7 Operations Center at 703.566.9463 or complete the form below.
Source: SEO Pressor




