Before you take a business trip to China, familiarize yourself with the risks associated with travel to the country, as well as guidance on the business culture and etiquette.
By Zev Faintuch, Senior Intelligence Analyst

|
JULY 27, 2023 INSIDE THIS ARTICLE, YOU'LL FIND: |
After nearly three years of some of the harshest travel restrictions in the world aimed at eradicating the coronavirus, China is once again open for business (and tourists). In March 2023, China resumed issuing visas to foreigners. Yet, the U.S. State Department issued a Level 3 travel alert for China in June 2023, urging travelers to “reconsider travel” due to the “arbitrary enforcement of local laws.” So, how should business travelers approach travel to China in this new and dynamic environment?
As business travel to China picks up, travelers would be well advised to familiarize themselves with the increasing legal and cyber risks, be mindful of China’s unique business etiquette and cultural sensitivities, and learn how to respond to these challenges to ensure a safe and successful visit and return home. China’s remarkable economic growth and its emergence as a global economic powerhouse have attracted the interest of business leaders and entrepreneurs worldwide. But as the geopolitical rivalry between China and the United States (U.S.) deepens, the window of opportunity for travel to China is starting to close.
Safety and Security Risks in China
In June, the U.S. State Department issued a Level 3 travel alert for China, urging travelers to “reconsider travel” due to the “arbitrary enforcement of local laws.” According to the State Department, foreigners traveling in China and Hong Kong, “including but not limited to businesspeople, former foreign government personnel, and journalists have been unjustly interrogated and detained” for alleged violations of Chinese national security laws. The risk of arbitrary detention is elevated for those with government, miliary, and military contractor experience, human rights lawyers, activists, and critics of the government. Dual nationals also face higher risk because the governments of China, Hong Kong, and Macau do not recognize dual nationality and may prevent the U.S. embassy or consulates from providing consular services. At this point, Global Guardian has begun to advise against travel on a case-by-case basis for individuals in the above-mentioned categories.
While China has low levels of crime, the preeminent risk to business travelers is cybercrime and cyber espionage. China’s state-sponsored hacking outfits are some of the most sophisticated in world. The government and many state-linked enterprises have expansive efforts in place to acquire U.S. technology, including sensitive trade secrets and intellectual property. If you are traveling to China for business purposes, you should assume that you are of interest to a hostile actor.
Travel Risk Management
Learn more about how Global Guardian’s travel risk management solutions can help you travel safer.
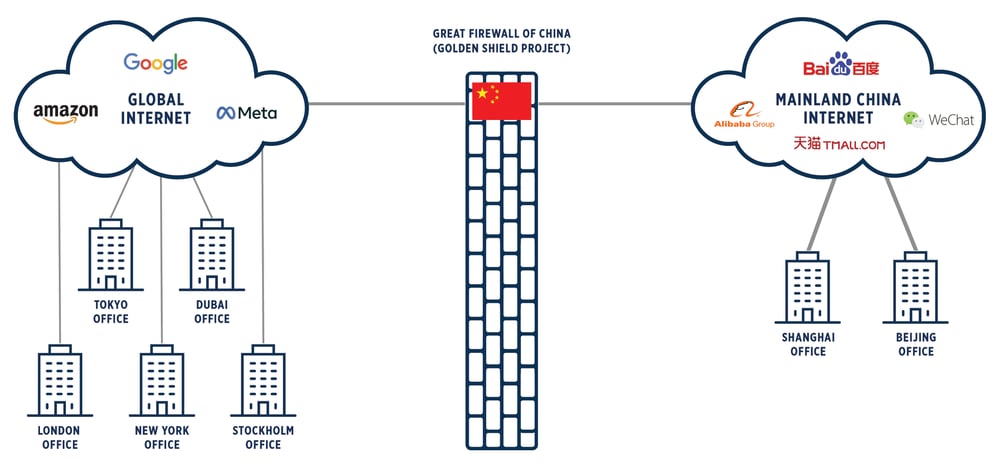
The Great Firewall of China
In the digital age, where the flow of information knows no borders, the Great Firewall of China stands as a symbol of a nation’s unique approach to internet censorship and control. Officially known as the Golden Shield Project, this extensive system of online restrictions, is designed to regulate and restrict online access within the country.
The Great Firewall operates through a combination of technical measures, including IP blocking, DNS filtering, keyword filtering, and deep packet inspection. These mechanisms allow the Chinese government to monitor, filter, and block access to specific websites, social media platforms, search engine results, and online content deemed sensitive or politically undesirable. The system also employs advanced technologies to track and identify individuals engaging in activities that violate Chinese regulations. Social media platforms, blogging sites, and messaging apps are closely monitored, with real-time content filtering to prevent the spread of information deemed harmful or subversive.
The firewall’s impact on international businesses, particularly in the tech sector, remains a topic of concern and debate. Despite the robustness of the Great Firewall, various techniques and tools, including virtual private networks (VPNs), proxy servers, and encrypted communication methods, are commonly used by tech-savvy individuals to access blocked content. The Chinese government has periodically cracked down on such tools, intensifying its efforts to maintain control over the information and communications landscape.
Advice for Mitigating Safety and Security Risks
In this section we take a look at the security risks travelers may face in China and offer advice on how these can be mitigated.
Inspections
The Chinese government or the security team of a host organization could compel travelers to log into their devices for inspection, raising the likelihood of compromise by malware.
Advice:
- Global Guardian can issue “burner” mobile devices to its clients who travel to high-risk locations
- Travelers are advised to only carry essential devices that are free of sensitive data. If sensitive data is necessary for a business trip this should be carried on a portable USB device with hardware-based encryption.
Unsecure networks
Hostile actors have access to networks, including hotel networks and WiFi. This raises the likelihood of sensitive information (sensitive files, passwords/credentials) being stolen.
Advice:
- If email is required, use trip-specific and non-enterprise secure email solutions. Create a dedicated account for travel and instruct colleagues and assistants to direct urgent messages to that account.
- Use secure encrypted messaging services (like Signal) instead of SMS or other insecure chat services.
- Enable two-factor authentication for access to your password manager.
- Consider using an Apple iPad or mobile phone instead of bringing a laptop.
- Use a portable USB device with hardware-based encryption to manage documents instead of accessing them over the cloud.
- If you bring a laptop, ensure that it and its applications are patched and make sure you enable hard drive encryption.
Surveillance
China possesses a sophisticated surveillance system based on a vast array of cameras and sensors, aided by facial and voice recognition software and artificial intelligence. There is a risk of very high-resolution cameras being trained on keyboards to capture login credentials and collect biometric information. USB charging ports in hotel rooms and public venues can also be used to access your devices in order to copy information or to install malware.
Advice:
- Use a dedicated VPN and diagnostic hardware on ALL mobile devices (smartphone, laptop, and tablet) at ALL times.
- Bring your own USB charging port for all foreign travel.
- Be mindful that you are ALWAYS being watched.
Understanding the Business Culture and ETIQUETTE in China
Understanding and embracing the business culture in China is crucial for anyone seeking to establish successful partnerships or ventures in this vibrant market. China’s rich history, deep-rooted traditions, and unique social dynamics significantly shape its business environment.
In the following section, we take a closer look at key aspects of Chinese business culture along with insights and etiquette for navigating this dynamic landscape.
GREETINGS: HOW TO MAKE A GOOD FIRST IMPRESSION
A traditional handshake is sufficient for both men and women in China. There is no need for hugs, kissing, or bowing as in some other East Asian cultures. A simple “nihao” or “hello” is adequate.
Business cards are customarily exchanged in China. Make sure to:
- Stand when exchanging cards.
- Have dual-sided Chinese translated cards (one side English, one side simplified Mandarin).
- Present the Chinese side face up using both hands.
- Always take the time to read a card after it is presented to you.
- NEVER write comments on another person’s business card.
- The most senior person begins the greetings. Greet the oldest, most senior person before others.
- In group introductions, line up according to seniority with the senior person at the head of the line.
- Use family names and titles to refer to yourself and colleagues (married women retain their maiden names).
- Chinese people point with an open hand. NEVER point with your index finger.
- Respect and reputation are paramount in Chinese culture. NEVER criticize, contradict, or upstage someone during a meeting.
Dining:
- Leaving a tip can embarrass the recipients, it may even be misinterpreted as a bribe (though tipping in Hong Kong is acceptable in high-end establishments).
- It is considered rude to place chopsticks standing up in a bowl (a symbol of death). Rest chopsticks on a chopstick holder instead.
Chinese Drinking Culture
- Alcohol is often used to facilitate business deals and is commonly consumed in social interactions.
- The host will typically make a toast to start the meal, and it is considered impolite to drink—or eat—before the host has made a toast. The first toast is often a "bottoms up" ("ganbei”) toast, which is a sign of respect and a way to start the meal or event. The "ganbei” demonstrates the sincerity of the toast.
- It is customary for the host or friends to refill each other's glasses to the brim whenever they are empty or a toast has been made. This is done even when it is not requested, as a sign of hospitality and respect. In general, younger drinkers should refill the glasses of those who are older or outrank them.
- Toast-making: it is customary to use the right hand as a sign of respect. The glass should be held at a lower position than the glasses of others, especially the host. For added formality, the left hand can be placed underneath the cup while it is being held by the right.
- The proper way to receive or offer a glass of alcohol is always with both hands.
- Politely abstaining: It is easier to refuse to drink more if a guest sets their limits at the beginning of the meal, rather than midway. One can also offer an excuse in advance (such as not feeling well, having an early morning the next day, or health problems) to make it clear that they will not be drinking much.
Guanxi: Building Relationships
Guanxi, or the concept of personal relationships, lies at the core of Chinese business culture. Building strong interpersonal connections is essential for conducting successful business transactions. Networking and establishing trust through socializing and mutual favors are considered integral to building guanxi. Business decisions are often influenced by these relationships, and it is common for individuals to prioritize personal connections over contracts or legal agreements.
Face: Preserving Dignity
The concept of “face” holds immense importance in Chinese society. It refers to one’s reputation, dignity, and social standing. Maintaining face is crucial in business interactions, as both parties strive to avoid embarrassment or loss of prestige. While in many Western countries, “telling it like it is” is considered a positive trait, in China, criticizing or humiliating someone publicly is strongly discouraged, as it can cause loss of face. Business deals have been lost over such a faux pas. Conversely, offering praise and demonstrating respect can help foster a positive business environment.
Hierarchy and Respect
Chinese business culture places significant emphasis on hierarchy and respect for authority. Age, position, and seniority hold great importance, and decision-making is often centralized within a hierarchical structure. It is essential to acknowledge and show deference to those in senior positions.
Using appropriate titles and honorifics when addressing business counterparts demonstrates respect and establishes a favorable impression. In China, the family name is listed first, followed by the given name. Using the example of Chinese President Xi Jinping, the name “Xi” is his family name while “Jinping” is his given name. It is considered respectful to refer to a Chinese person by their family name; in this case: Mr./President Xi.
Communication Styles
Chinese communication styles may differ from those in Western cultures. Indirect communication, where messages are conveyed subtly or through non-verbal cues, is common. It is crucial to read between the lines and pay attention to non-verbal cues such as facial expressions and body language. Additionally, maintaining harmony and avoiding conflict is highly valued. Criticism or direct refusals may be expressed implicitly, or in private, to preserve relationships.
Patience and Long-Term Vision
Doing business in China requires patience and a long-term perspective. Chinese businesspeople tend to prioritize building strong foundations and establishing trust before engaging in significant transactions. Quick deals may be viewed with suspicion, as trust and reliability are key factors in successful business relationships. Investing time and effort into relationship-building can yield substantial returns in the long run.
Gift-Giving and Etiquette
Gift-giving is deeply ingrained in Chinese culture and plays a vital role in business interactions. When presenting gifts, it is essential to consider cultural norms and avoid items that may be seen as inappropriate or symbolic of negative connotations. Red envelopes containing money are often given during festive occasions or to mark significant milestones. It is customary to reciprocate gestures of gift-giving.
Things to Know When Traveling in China
From currency and transportation to internet access and political sensitivities, the following are seven things to generally know before you embark on a trip to China.
1. Visa REQUIREMENTS AND Documentation
Before traveling to China, it is important to research and understand the visa requirements for your nationality. Most visitors will require a visa, which can be obtained from Chinese embassies or consulates. Ensure that your passport is valid for at least six months beyond your intended departure date and carry all necessary travel documents, including your visa, at all times during your stay.
2. Language and Communication
Mandarin Chinese is the official language. English proficiency varies across different regions of China. In major cities and tourist areas, you might find people who can communicate in English, but it is advisable to learn a few basic Mandarin phrases or carry a translation app to facilitate interactions with locals. Having a few key phrases written down can be helpful when seeking directions or ordering food.
3. Currency and Payment Options
The official currency in China is the Chinese Yuan. Cash is widely accepted, especially in smaller establishments and local markets, so it is advisable to carry some Chinese Yuan with you. Major credit cards are accepted in hotels, upscale restaurants, and larger retail outlets, but may not be widely accepted in more remote areas. Mobile payment platforms like WeChat Pay and Alipay are prevalent throughout China and offer convenient payment options.
4. Internet Access and VPNs
Internet access in China is widespread, but certain websites and social media platforms, including Google, Facebook, Twitter, and Instagram, are subject to restrictions. To access blocked websites and maintain internet privacy, consider using a VPN service before arriving in China. VPN usage is subject to periodic restrictions, and it is advisable to research reliable VPN options before your trip.
5. Transportation and Getting Around
China’s vast size and efficient transportation network offer various options for getting around. High-speed trains connect major cities, providing a convenient and comfortable mode of transportation. Public transportation systems, including subways and buses, are well-developed in urban areas, offering affordable travel options. Taxis and ride-hailing services like Didi are prevalent but ensure that you have the destination address written in Mandarin for easier communication with drivers.
6. Etiquette and Cultural Considerations
Respecting Chinese customs and cultural norms is essential when traveling in China. Some key points to remember include:
- Demonstrate politeness and use appropriate greetings.
- Avoid sensitive topics such as politics or criticism of the Chinese government.
- Respect religious and cultural sites, remove shoes when required, and dress modestly in places of worship.
- Take cues from locals regarding queueing, as lines may not be as strictly followed in all situations.
- Exercise caution with public displays of affection, as they may be considered inappropriate in certain areas.
7. Political Sensitivities
According to the State Department, “Security personnel may detain and/or deport U.S. citizens for sending private electronic messages critical of the PRC, Hong Kong SAR, or Macau SAR governments.” Travelers to China should:
- Refrain from engaging in political discussion in general.
- Refrain from discussing the origins of and culpability for the Covid-19 pandemic.
- Do not refer to Hong Kong, Macau, Taiwan, and Tibet as independent “countries.”
- Prior to travel delete social media posts that could be deemed politically sensitive. Examples of such topics include religious freedoms, Taiwan, Tibet, Hong Kong, U.S.-China relations, Xinjian province (Uyghur minority), North Korea, political systems/ideology (communism/socialism, democracy, etc.), and, most importantly, the Chinese Communist Party (CCP).
Navigating the business culture in China requires a deep appreciation for the values, customs, and social dynamics that shape this dynamic market. Understanding the significance of guanxi, face, hierarchy, and communication styles lays the foundation for successful business interactions. Adhering to cultural norms and demonstrating respect and patience are key to fostering long-term relationships. But at the same time, security is paramount. One should assume and act as if they are constantly being surveilled when in China. In order to mitigate security risks, businesses should perform risk assessments on all high-level employees to ascertain risk/benefit of a trip—how important is it for your employee to travel to China?
Geopolitical events, specifically current trends in U.S.-China relations, should be closely monitored as the risk of arbitrary detention is linked to the current state of relations. Scenario planning should be conducted, and a plan put in place in the event of an arbitrary detention/exit ban. If you have previously or currently work in the fields of government, miliary, or military contractor, human rights law, activism, or have been a vocal regime critic, then you should reconsider travel to China for your own safety.
"In order to mitigate security risks, businesses should perform risk assessments on all high-level employees to ascertain risk/benefit of a trip—how important is it for your employee to travel to China?"
The clock is ticking. It is unclear for how much longer business travel to China under the current paradigm will be possible. So, if you had to put off a business trip to China due to the tight Covid-19 entry restrictions, now is your opportunity to visit before it’s too late.
Standing by to Support
The Global Guardian team is standing by to support your security and medical requirements when traveling to and staying in China, including:
- Duty of Care Membership
- Custom Intelligence
- 24/7 Cyber Monitoring, Hunting, and Response
- Executive Protection and Transportation
To learn more about our pre-trip and crisis response services, complete the form below or call us at + 1 (703) 566-9463.